Rancher 2: Let's Encrypt with Ingress-Nginx & Cert-manager

Alright... It's one of the simplest things I lost the most time on during my rancher tests. I couldn't find any documentation/tutorial that worked properly for the first time. Here is mine by mixing all of this information! The goal is to set and automatically renew Let's Encrypt when we add an Nginx reverse proxy via rancher on a service/workload
Prerequisite
Everything we set up in the previous article :
- Rancher 2.0 & Kubernetes Cluster
- Kubectl and kube_config_cluster.yml
- Helm
- Ndd redirect server (A entry)
Purge old installations
We will start by cleaning up any old cert manager installation. In this tutorial we will work on version 0.15.0 of Cert Manager, remember to change the number in the url required.
# with helm
helm --namespace cert-manager delete cert-manager
kubectl delete namespace cert-manager
# with kubectl
kubectl delete -f https://github.com/jetstack/cert-manager/releases/download/v0.15.0/cert-manager.yaml
kubectl delete apiservice v1beta1.webhook.cert-manager.io
kubectl delete namespace cert-manager
# by security : issuer
kubectl delete letsencrypt-staging
kubectl delete letsencrypt-prod
kubectl delete issuers.cert-manager.io letsencrypt-staging
kubectl delete issuers.cert-manager.io letsencrypt-prodNormally, you will get something like this
kubectl get all -n cert-manager
> No resources found.Install cert-manager
# with helm
kubectl create namespace cert-manager
helm repo add jetstack https://charts.jetstack.io
helm repo update
helm install
\ cert-manager jetstack/cert-manager
\ --namespace cert-manager
\ --version v0.15.0
\ # --set installCRDs=true
# with kubectl
kubectl apply --validate=false -f https://github.com/jetstack/cert-manager/releases/download/v0.15.0/cert-manager.yamlResult expected :
kubectl get all -n cert-manager
NAME READY STATUS RESTARTS AGE
cert-manager-5c6866597-zw7kh 1/1 Running 0 2m
cert-manager-cainjector-577f6d9fd7-tr77l 1/1 Running 0 2m
cert-manager-webhook-787858fcdb-nlzsq 1/1 Running 0 2mAdd Let's Encrypt Issuer
We will set up two issuers for Let’s Encrypt, Staging for our test, and Production. Be careful with production, there is limits.
kubectl create --namespace default --edit -f https://cert-manager.io/docs/tutorials/acme/example/staging-issuer.yaml
# edit mail and save
kubectl create --namespace default --edit -f https://cert-manager.io/docs/tutorials/acme/example/production-issuer.yaml
# edit mail and save you need to add this for all namespace needed with namespace option.
Result :
kubectl describe issuers.cert-manager.io letsencrypt-staging
Name: letsencrypt-staging
Namespace: default
Labels: <none>
Annotations: <none>
API Version: cert-manager.io/v1alpha3
.....
kubectl describe issuers.cert-manager.io letsencrypt-prod
Name: letsencrypt-staging
Namespace: default
Labels: <none>
Annotations: <none>
API Version: cert-manager.io/v1alpha3
.....
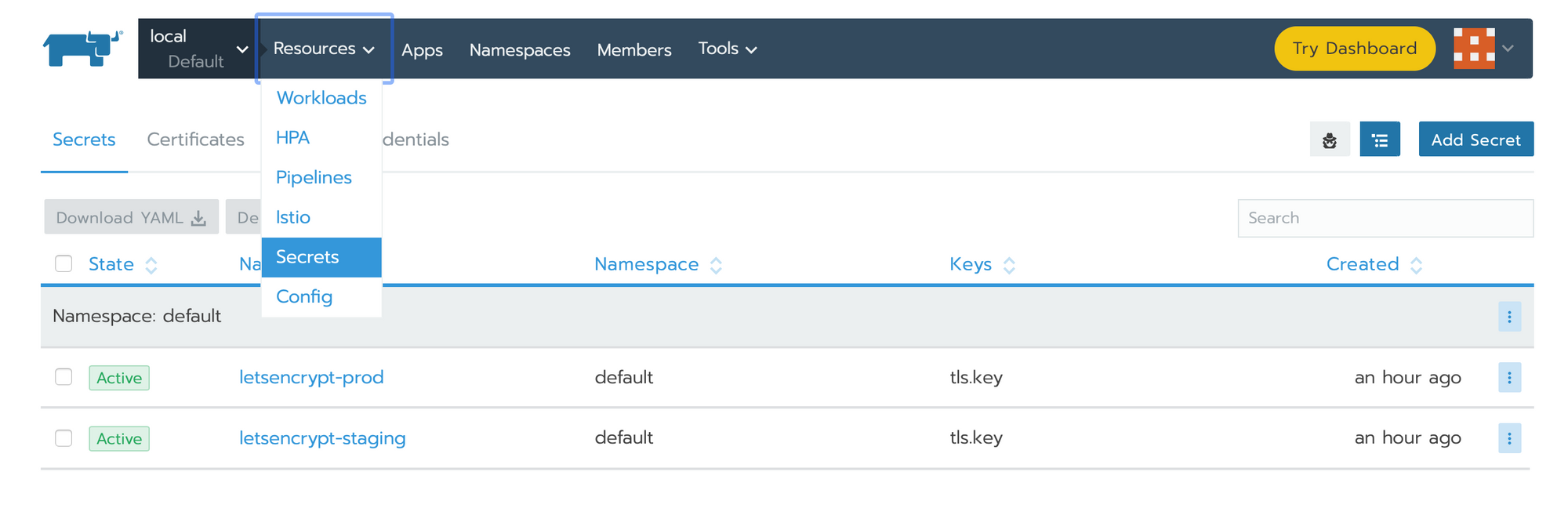
Create a workflow ( just for example )
- Go in rancher > local > default > workloads
- Click on Deploy
- Set an Name : app-domain-com
- Namespace : default
- Click on Add Port
Port Name : app-domain-com-port
Publish the container port : 2368
Protocol : TCP
As a : NodePort
On listening port : Random
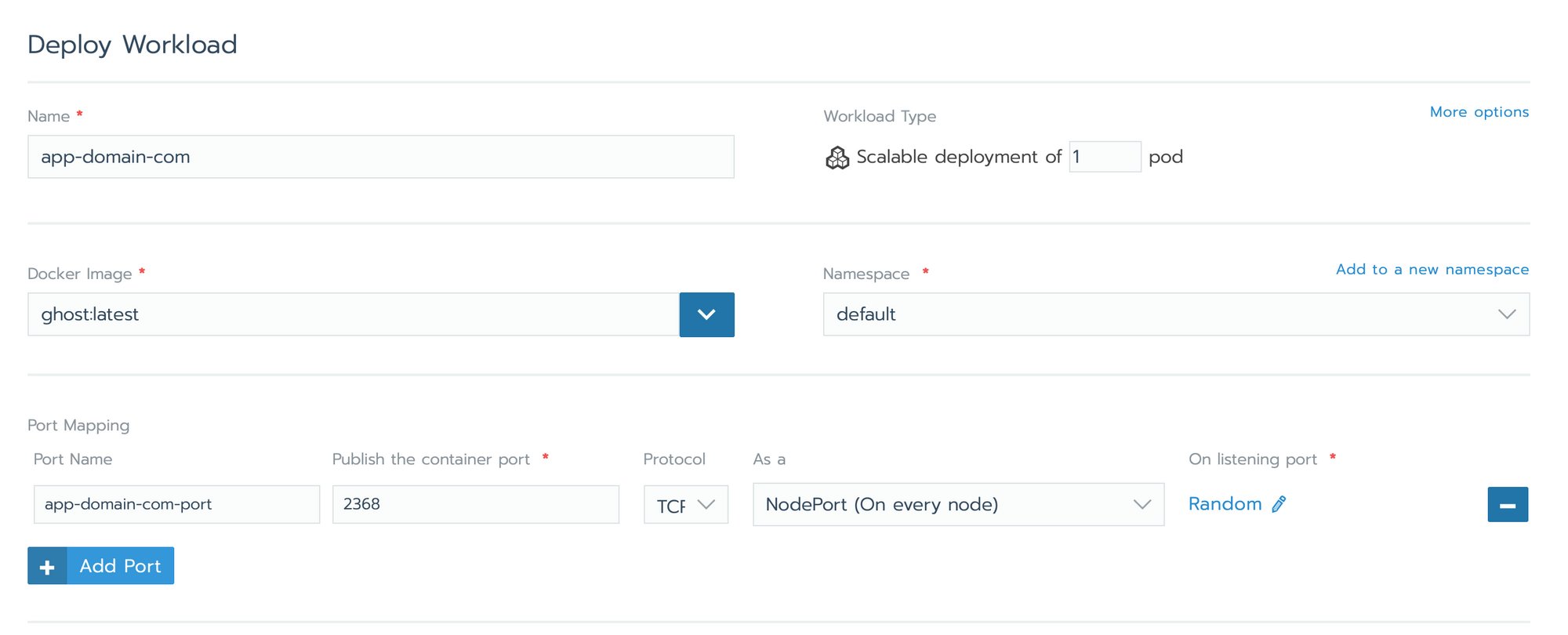
- Set Environment Variables
url : https://app.domain.com
- Click on Launch
Result expected :
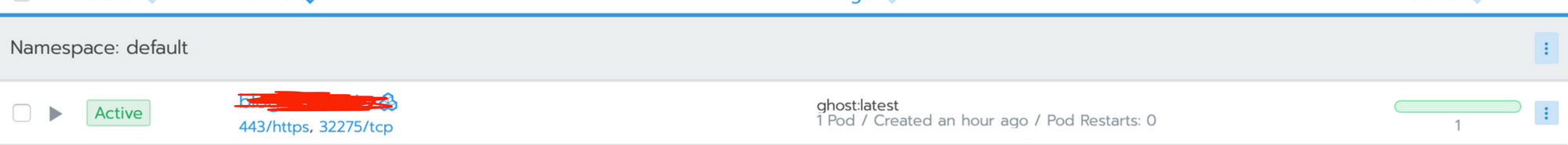
Create Load Balancer
- Go in rancher > local > default > Load Balancing
- Click on Add Ingress
- Set an Name : app-domain-com
- Namespace : default
- Click on Add Service (and remove old line)
Path: Empty
Target: app-domain-com-nodeport
Port: App-domain-port- Set SSL/TLS Certificates
- Click on Add Certificate
url : app.domain.com- Click on Save
Result expected :
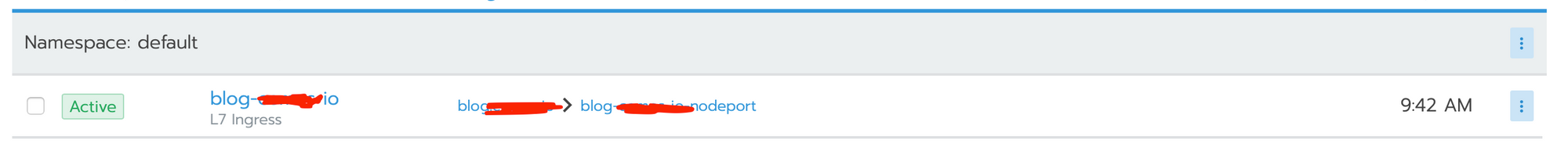
Set cetificate to Let's Encrypt
- Go in rancher > local > default > Load Balancing
- click on three dots options of your Load Balancer and select View/Edit YAML
- Add :
# in metadata > annotations:
cert-manager.io/issuer: letsencrypt-staging
# in tls > hosts:
secretName: app-domain-com-tls
- Click on save, wait a minute, normally cert-manager will temporarily create a new Ingress.
- It shoudl work
Result expected :
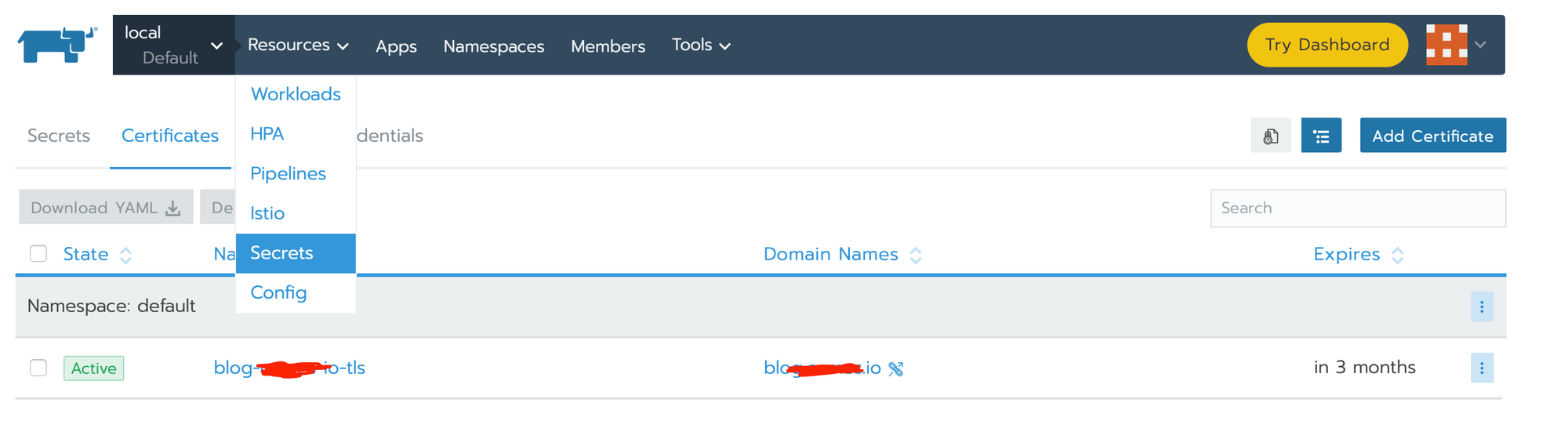
cert-manager.io/issuer-name: letsencrypt-prod
If everything is ok, you can switch to prod :)
Sources
Update :